08 Apr 2021
Welcome to the website of David Wolf. With over 15 years of Web Development, BI, and IT experience, and over 5 years of Healthcare experience, I’m always looking to grow.
Experience in product marketing, agile development and web usability standards.
Expertise in responsive website development from discovery to production, BI analytical dashboards, and digital project management.
Interests in cryptology and cryptocurrency, specifically coins promoting proof of stake (PoS) and block-lattice chain structuring.
I enjoy snowboarding, playing guitar, and spending time with my family.
You can reach me at iam@dglw.net, Twitter, and Linked In.
_David Wolf
05 Apr 2021
As a lot of my friends, I have become the resident IT expert for my family. This means I may get called upon to handle all technical requests, from accessing email to troubleshooting the dreaded Windows blue-screen-of-death. In my most recent attempt, my parents warned me that something was “very wrong with the computer this time.” Remote Destkop was not responding, so I took a drive to visit my parents and see what the problem was, and on the desktop background was a glaring message that read something of the following:
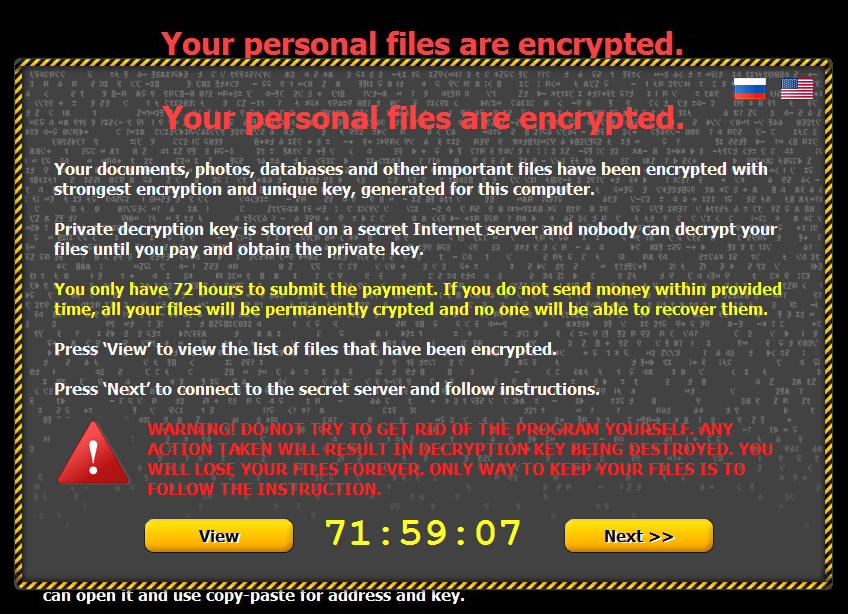
My parents had become victims of Ransomware.
This can happen by generally (a) downloading a malicious package via an untrusted but well-disguised email, or (b) through an Adobe Flash vulnerability. The later is not suprising to most techs, as flash has been known to have vulnerabilities, the latest being a huge vulnerability that may lead to remote root access to your machine.
When first run, the ransomware installs itself in the user profile folder, adding a key to the registry that causes it to run on startup. It then attempts to contact one of several designated command and control servers; once connected, the server generates a 2048-bit RSA key pair, and sends the public key back to the infected computer.The program then encrypts files across local hard drives and mapped network drives with the public key, and logs each file encrypted to a registry key.
Swiftly checking their documents folder, all of my parents files had been encrypted. Every. single. one. Scrubbing the registry had no effect, and I was unaware of the steps that were being taken in Operation Tovar to disrupt the botnet that controlled the flavor of Ransomware that had infected my parent’s computer.
Since, after being consulted, my parents refused to pay the ransom, the only thing that saved my parent’s personal files was the auto-backup that I enabled when I first provisioned their Windows machine. Re-installing the OS with a clean backup was the only option that allowed me to save my parents personal documents.
Two lessons to this story:
- Don't open any email attachment in which you are not 100% sure of the sender identity.
- Setup an auto-backup service to protect your files in the case of cataclysmic failure.
